Most of these apps listed here are underground hacker software which you cannot find anywhere but the darknet. We have brought you software that is prolific on the dark web.
In a world ruled by technology, have you ever wondered how secure your phone really is? How can hackers infiltrate your personal space and access your confidential information? “How hackers can hack into phones and what to know for you to protect yourself” is a pressing concern in today’s digital age, and this article aims to shed light on this vital topic, unraveling the intricate methods employed by hackers and offering robust solutions to safeguard your privacy.
To offer a brief glimpse into this realm, hackers use sophisticated techniques like phishing, malware, and spyware to access sensitive information.
There are underground hacking tools that hackers use which we will name.
Tools for Hacking that You Need to Know About
The first on the list is Sphnix
Sphnix Hacking tool
Sphinx is a sophisticated hacking tool designed specifically for mobile devices, targeting both Android and iOS platforms. It has gained attention within the cybersecurity community due to its advanced capabilities and its potential to compromise the security of smartphones.
Watch the video of how the hackers did it.
Sure, here’s the rewritten version:
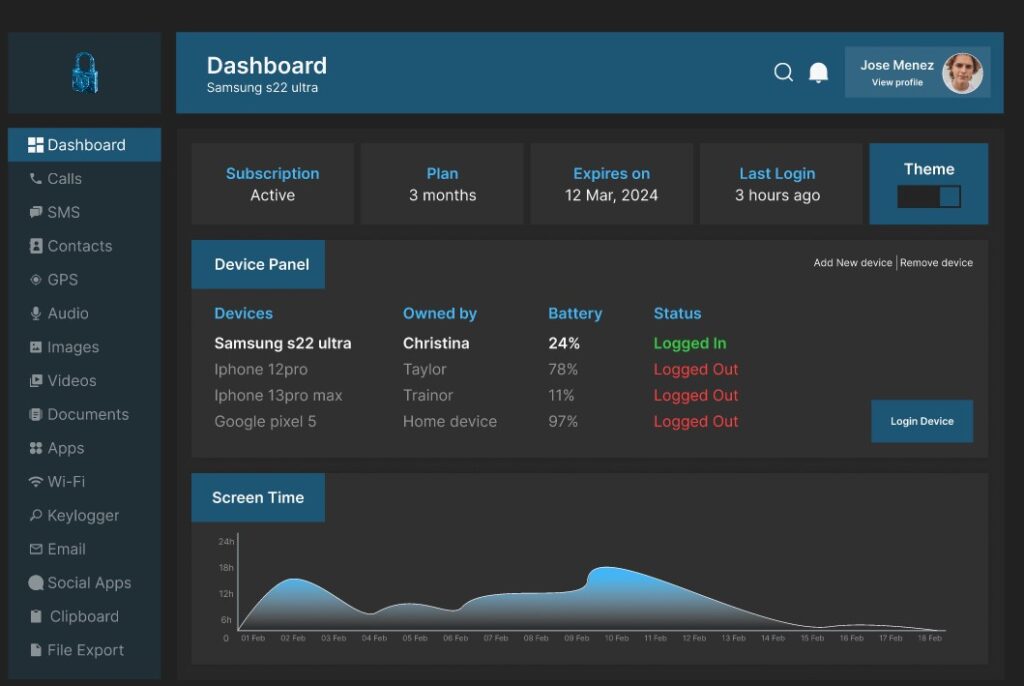
How Target is Monitored
To monitor the target phone, is through online dashboard.
USB Unlocker
This device is a plug-and-play hardware that allows for unlocking of device passwords. From the video description, you can unlock a phone easily within few minutes.
Watch the demonstration of USB unlocked.
The use of this software is very powerful if someone get its hands on it. This is why you need to be aware of who you give your phones to. A few minutes, anyone can extract information without you being aware that sensitive data has been extracted.
Z Spy
Z Spy is a claimed underground hacking software that uses only a phone number to hack a cell phone. There are news on the dark net that it’s very powerful. This is why security tips need to bring you awareness and evidence of possible hacking by this hackers.
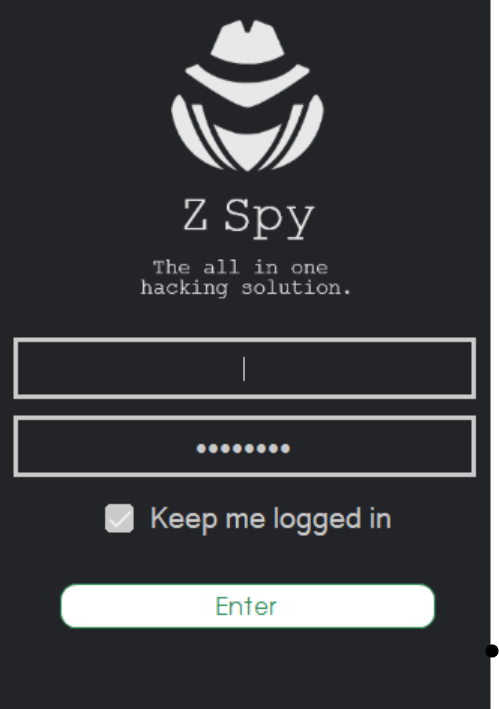
This are some of the software that hackers uses to hack a cell phone without touching it.
There are some software that you might want to be also aware of. They need to touch the phone before they can work
Mspy: A Closer Look
4.1 Features of Mspy
Mspy is one of the most popular phone monitoring apps available. It offers features like call tracking, message monitoring, and even the ability to track social media activities.

Installation Process
Installing Mspy on a target device requires physical access to it. Once installed, it operates in stealth mode, making it challenging for the device owner to detect its presence.
The installation typically involves the following steps:
- Subscription: Purchase a subscription plan from Mspy’s official website.
- Download: Download and install the Mspy app on the target device.
- Configuration: Set up the app according to your monitoring preferences.
- Monitoring: Once configured, Mspy starts collecting data from the target device, which you can access through a secure online portal.
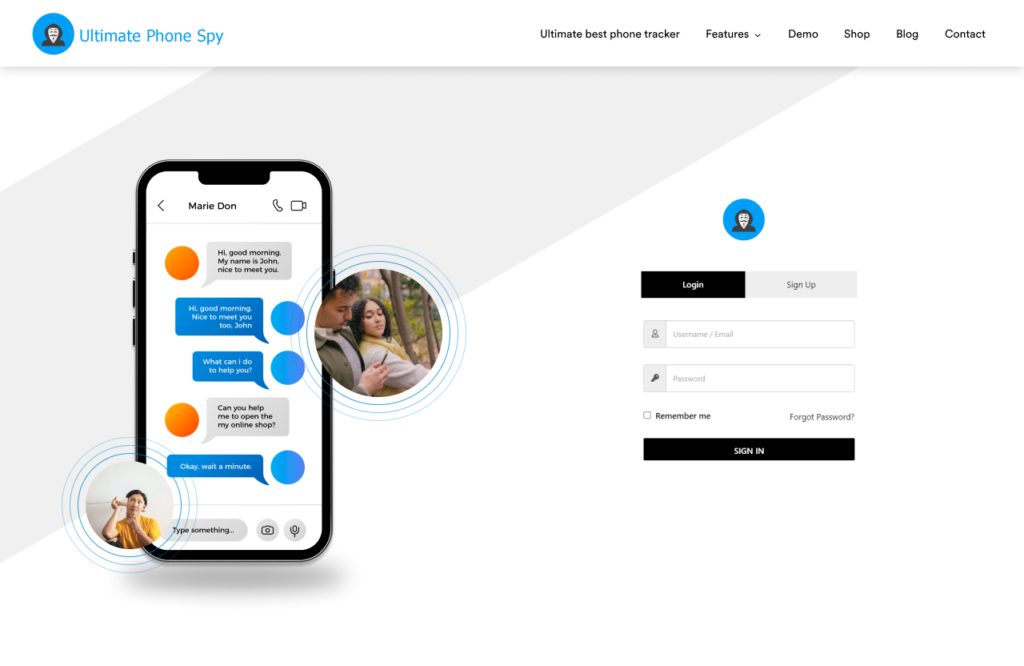
Ultimate Phone Spy: Monitoring Made Easy
Key Features
Ultimate Phone Spy boasts a user-friendly interface and a wide array of monitoring features. Users can access detailed call logs, text messages, and even multimedia files.
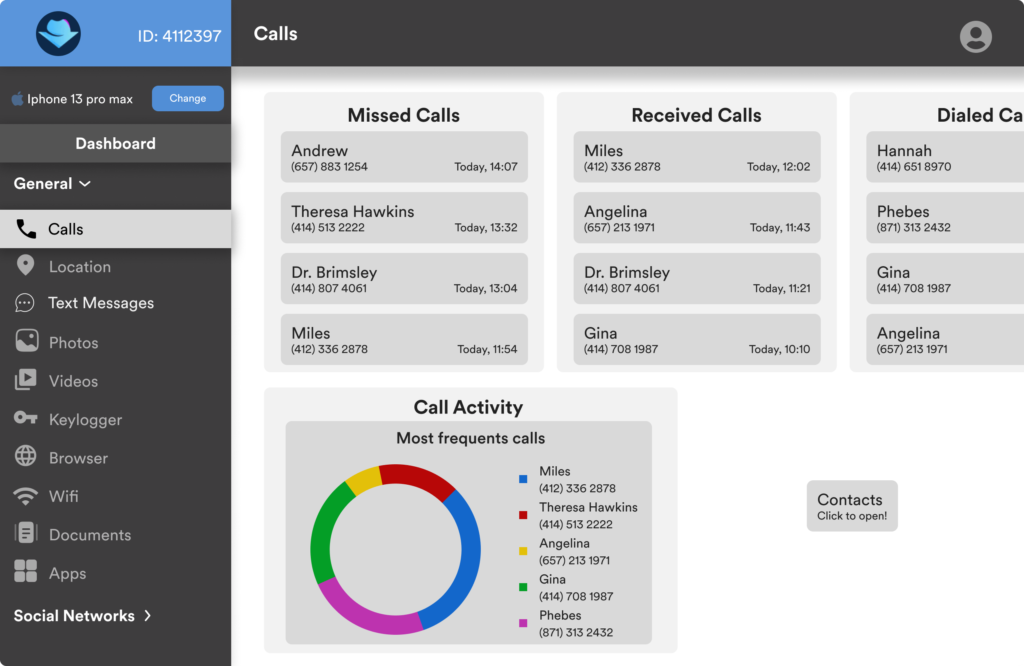
- Call Logs: Access detailed call logs, including call duration, contact information, and timestamps.
- Message Tracking: Read both incoming and outgoing messages, including those from messaging apps.
- Multimedia Access: View multimedia files such as photos and videos stored on the target device.
- Remote Control: Some apps allow you to perform actions remotely, such as locking the device or wiping data.
Setting Up Ultimate Phone Spy
Getting started with Ultimate Phone Spy is relatively straightforward:
- Subscription: Purchase a subscription plan from the official Ultimate Phone Spy website.
- Installation: Download and install the app on the target device, following the provided instructions.
- Configuration: Customize the settings to monitor specific activities.
- Monitoring: Once configured, the app silently collects data, which you can access through a secure online dashboard.
Nova Spy App: Stealthy Surveillance
Nova Spy Features
Nova Spy App prides itself on its stealthy operation. It allows users to monitor everything from texts and calls to internet browsing history.
How to Get Started
Setting up Nova Spy App involves a few simple steps. Users must subscribe to the service, install the app on the target device, and configure the settings.
Alternatives to Phone Monitoring Apps
If you have concerns about using phone monitoring apps or if you believe they may not be the right solution for your situation, consider these alternatives:
Open Communication
The foundation of any healthy relationship is open and honest communication. Instead of resorting to monitoring apps, discuss your concerns and fears with the involved party.
Trust-Building
Building trust is a crucial aspect of personal relationships. Work on establishing trust through mutual respect, transparency, and understanding.
Seeking Professional Help
If you suspect serious issues in a relationship, consider seeking the guidance of a professional therapist or counselor. They can provide insights and strategies for resolving issues.
Legitimate Use Cases
Before diving into the technicalities of these apps, it’s crucial to understand their legitimate use cases. Here are some scenarios where phone monitoring apps can be used responsibly:
- Parental Control: Parents can use these apps to ensure their children’s safety online and monitor their activities.
- Employee Monitoring: Employers may employ these apps to track company-owned devices and ensure employees are using them for work-related purposes.
- Lost or Stolen Phones: Tracking apps can help locate a lost or stolen device, protecting personal data.
However, these apps should always be used within the bounds of the law and with the consent of the device owner.
The Controversy Surrounding Phone Hacking
Ethical Concerns
The use of phone monitoring apps raises ethical questions. Invasion of privacy and the violation of personal boundaries are primary concerns. It is essential to weigh the need for monitoring against the right to privacy.
Using these apps without the knowledge and consent of the person being monitored can strain personal relationships and lead to trust issues. Clear communication about the intention to use such apps is essential.
Legal Implications
The legality of using these apps varies from place to place. Some jurisdictions strictly regulate their usage, while others have no clear laws. Engaging in phone hacking without proper authorization can lead to serious legal consequences, including fines and even imprisonment in some cases.
Before using any monitoring app, it is essential to research and understand the legal implications in your area. Always err on the side of caution and legality.
Alternatives to Phone Monitoring Apps
If you have concerns about using phone monitoring apps or if you believe they may not be the right solution for your situation, consider these alternatives:
Open Communication
The foundation of any healthy relationship is open and honest communication. Instead of resorting to monitoring apps, discuss your concerns and fears with the involved party.
Trust-Building
Building trust is a crucial aspect of personal relationships. Work on establishing trust through mutual respect, transparency, and understanding.
Seeking Professional Help
If you suspect serious issues in a relationship, consider seeking the guidance of a professional therapist or counselor. They can provide insights and strategies for resolving issues.
Conclusion
In conclusion, phone monitoring apps like Mspy, Ultimate Phone Spy, and Nova Spy App can be powerful tools for specific purposes. However, they come with ethical and legal responsibilities. Always use them with consent, transparency, and within the confines of the law.
Balancing the need for monitoring with respect for privacy is essential to maintaining healthy relationships and respecting individual rights.
